Most people use username/password authentication for every day use. Whether it be email, social media, banking information or computer login, username and passwords are the most generalized and widely known form of security. However, username/password authentication are extremely basic. According to CNN news, these are the Top 10 Passwords used in 2019:
The top 10 most common passwords of 2019:
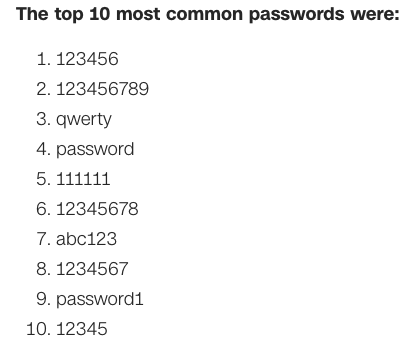
While this is somewhat humorous, it is important to recognize that usernames and passwords are easily hacked and are the source of many data breaches.
But it doesn't have to be this way -There are other forms of security that provide much more stringent authentication. For example, public key authentication. Even the longest passwords pale in comparison to public and private key authentications.
What is public key authentication?
For public key authentication, an SSH key pair is generated by the computer. This includes a public and private key which are cryptographic. The public key is stored on the SSH server and the public key is stored on the SSH client.
According to SSH.com, public and private SSH keys work like this:
"A public key that is copied to the SSH server(s). Anyone with a copy of the public key can encrypt data which can then only be read by the person who holds the corresponding private key. Once an SSH server receives a public key from a user and considers the key trustworthy, the server marks the key as authorized in its authorized_keys file. Such keys are called authorized keys. A private key that remains (only) with the user. The possession of this key is proof of the user's identity. Only a user in possession of a private key that corresponds to the public key at the server will be able to authenticate successfully. The private keys need to be stored and handled carefully, and no copies of the private key should be distributed. The private keys used for user authentication are called identity keys."
A few benefits of public key authentication:
-Superior to even the longest passwords.
-Backed by trusted cryptographic algorithms
-Automatic logon capabilities, you don’t have to try to remember your password!
How does Public / Private Key work?
For public/private key authentication, the SSH client software being authenticated has a public and a private key. The public key is stored on the server, and the private key remains on the client.
When the public key is mapped to a Windows user account, it provides automatic logon.
General Steps to Creating a Public / Private Key:
-
Generate a Public/Private Key Pair
-
Install the private Key on the SSH Client
-
Install the Public Key on the SSH Server
-
Map the Public Key to a Windows User Account to provide automatic logon
For detailed steps on setting up your GSW Public/Private Keys, visit here.