GSW Business Tunnel - Example Guide
Table of Contents
- Dynamic Forwarding Examples
-
-
- Local Forwarding Examples
-
- L01- Make a Telnet Connection Secure using the GSW Business Tunnel
- L02- Securely Access Blocked Website from Headquarters (blocked by company proxy filter)
- L03- Securely Access Blocked Website from Home due to Company Proxy Filter
- L04- Securely Access Email from Anywhere
- L05- Securely Remote Desktop to Work from Anywhere
-
- Remote Forwarding Examples
-
- R01- Securely Browse the company intranet from home, even though company does not allow incoming connections
- R02- Browse the Company Intranet from Sales Branch
- R03- Browse the Company Intranet from a Sales Branch 2
- R04- Browse the Company Intranet from Home
- R05- Browse the Company Intranet from Sales Branch using address 0.0.0.0
-
- Micro-Explanation Videos
-
Dynamic Forwarding Examples
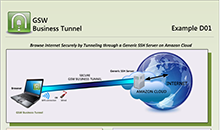
Tunnel Example D01
Securely Browse the Internet by Tunneling through a Generic SSH Server on Amazon Cloud
Case: Matt is on vacation. But his company needs him to run payroll today. He does not want to risk accessing payroll via non-secure internet access. Matt can create a secure tunnel for his laptop to access his companies payroll website.
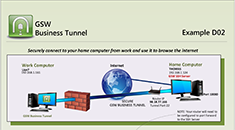
Tunnel Example D02
Securely connect to your home computer from work and use it to browse the internet
Case: Your company firewall blocks all internet browsing. You have received permission to access certain web sites for work, but company policy will not allow the firewall to be opened up to HTTP traffic. The company firewall is open to SSH traffic. You can create a secure tunnel to a SSH server located at home (or anywhere else that you have access) and browse the internet.
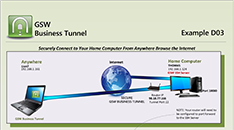
Tunnel Example D03
Securely Connect to Your Home Computer From Anywhere Browse the Internet
Case: Connect to your Home Computer from Anywhere and Browse the Internet You are traveling and want to Remote Desktop to your home computer. You can do this from anywhere using the GSW Business Tunnel. **Note: This example is the same configuration as D02.
Local Forwarding Examples
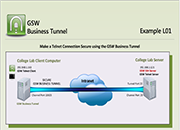
Tunnel Example L01
Make a Telnet Connection Secure using the GSW Business Tunnel
Case: A local technical college wants to demonstrate how you can secure telnet with an SSH Tunnel. In the technical lab they set up a telnet connection and use a network monitoring tool to observe the data. Then as shown in this example they set up the GSW Business Tunnel and then create the Telnet connection. Now when they monitor the line the data is encrypted
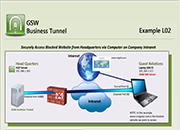
Tunnel Example L02
Securely Access Blocked Website from Headquarters via Computer on Company Intranet
Case: Access to www.craigslist.com is blocked by the company proxy filter in Headquarters. However, the company has some older office furniture for sale on craigslist. The facilities manager wants to view the ad. He knows that the training laptop on the company intranet in the guest relations building has access to the internet and is running the GSW SSH Server. The HQ7 (running the GSW Business Tunnel) creates a tunnel to the Guest Relations Laptop (GRLT) which is running the GSW SSH Server and has access to www.craigslist.com

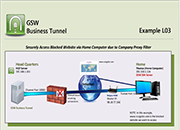
Tunnel Example L03
Securely Access Blocked Website via Home Computer due to Company Proxy Filter
Case: Access to www.craigslist.com is blocked by the company proxy filter at Head Quarters. However, the facilities manager needs to access craigslist to find old desks for sale in the area. His computer (Thomas) at home is running the GSW SSH Server. The developer can create a Tunnel to his home computer and then browse www.craigslist.com from HQ7.

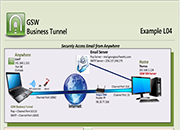
Tunnel Example L04
Securely Access Email from Anywhere
Case: Create a secure GSW Business Tunnel to a secure SSH Server and check/send email. In this example you could be at a public Wi-Fi location, a hospital, airport, library, coffee shop or at a corporate business partners site. You can use your Business Tunnel to ensure a secure connection to a safe location to check/send email. This example requires 2 channels to be used with one Tunnel.
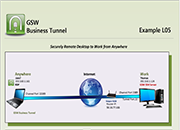
Tunnel Example L05
Securely Remote Desktop to Work from Anywhere
Case: You are a traveling and want to Remote Desktop to your work computer. You can do this from anywhere using the GSW Business Tunnel.
Remote Forwarding Examples
Tunnel Example R01
Securely Browse the Company Intranet From Home, Even Though Company Does Not Allow Incoming Connections
Case: Your company does not allow incoming connections. You can set up the GSW Business Tunnel from work so that you can browse the company intranet from home. The Web Server is on the same computer as the Business Tunnel.

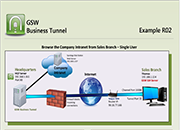
Tunnel Example R02
Browse the Company Intranet from Sales Branch – Single User
Case: Your company Headquarters (HQ) does not allow incoming connections. You can set up a tunnel from HQ so an employee can browse the company intranet from a new sales branch on the server (Thomas). The GSW Business Tunnel is on HQ7, a different computer than the web server(Synology Disk Station).

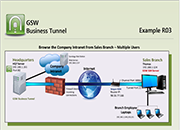
Tunnel Example R03
Browse the Company Intranet from Sales Branch – Multiple Users
Case:Your company Headquarters does not allow incoming connections. You can set up a tunnel from work (HQ7) so multiple employees can browse the company intranet from a new sales branch. The GSW Business Tunnel is on HQ7, a different computer than the web server(Synology Disk Station).

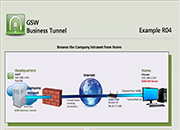
Tunnel Example R04
Browse the Company Intranet from Home
Case: Your company Headquarters does not allow incoming connections. You can set up a tunnel from work (HQ) so you can browse the company intranet from home. The GSW SSH Server and Web Server are on the same computer.

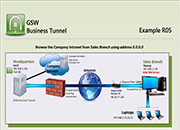
Tunnel Example R05
Browse the Company Intranet from Sales Branch using address 0.0.0.0
Case: Your company Headquarters does not allow incoming connections. You can set up a tunnel from work Headquarters so multiple employees can browse the company intranet from a new sales branch. The GSW Business Tunnel is on a different computer than the web server.

Micro Explanation Videos
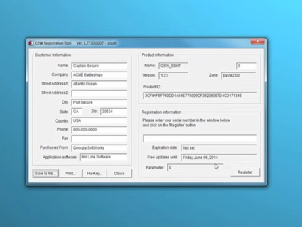
Micro Explanation Video: How to Install and Register the GSW Business Tunnel.
How Do You Install and Register the Georgia SoftWorks Business Tunnel?
The Business Tunnel is an SSH tunnel that provides businesses secure access to required network services that are often risky due to non-secure locations or unavailable due to policy configurations.
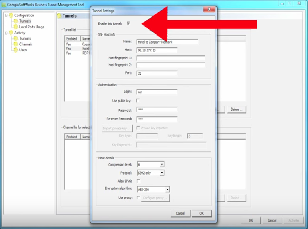
Micro Explanation Video: Tunnel Management
How Do You Manage Tunnels and Channels With the Georgia SoftWorks Business Tunnel?
The Business Tunnel is an SSH tunnel that provides businesses secure access to required network services that are often risky due to non-secure locations or unavailable due to policy configurations.

Micro Explanation Video: How SSH Tunneling Works
How Does SSH Tunneling work?
The Business Tunnel is an SSH tunnel that provides businesses secure access to required network services that are often risky due to non-secure locations or unavailable due to policy configurations.
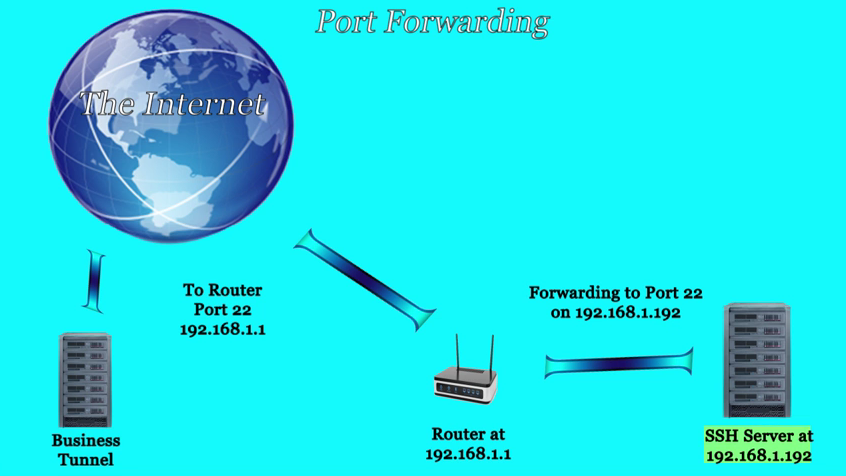
Micro Explanation Video: Port Fowarding a Router
How Do I Connect via SSH to a Server That is Behind a Public Facing Router?
This video shows you how to configure Port Forwarding on a public facing router to forward Business Tunnel connections to an SSH server.

Micro Explanation Video: Using a Host Fingerprint
What is a Host Fingerprint, and How Do I Implement One?
This video describes what a Host Fingerprint is, how it can make authentication between a server and client more secure, and how to configure a Host Fingerprint for use with the Georgia SoftWorks Business Tunnel.
Micro Explanation Video: Using Public Key Authentication
How Do I Authenticate Using a Public and Private Key Pair?
This video describes how to use key pairs to authenticate your GSW Business Tunnel.